Python 1st mid sem exam of 3rd semester Under Ranchi University
Topics covered in this blog
- Keywords and Identifiers
- Data types and its function
- List and its function
- Dictionary and its function
- Conditional construct
- Indentation and Commands
- Practical Question
Keywords and Identifiers
Python has a set of keywords that are reserved words that cannot
be used as variable names, function names or any other identifiers.
Keywords and Description
and = A logical operator.
as = The as
keyword is used to create an alias. when importing the module. For example -
import calendar as c
print(c.month_name[1])
We can refer to the calendar module and now we can refer to the calendar
module by using a instead of calendar.
assert = The
assert keyword is used when debugging the code.
The assert keyword
lets you test if a condition in your code returns. True, if not, the
programmer will raised an assertion error.
For example -
x = "Hello"
#if condition returns True, then nothing happens
asser x == "Hello"
#if condition returns false, assertion error is raised.
assert x == "goodbye"
break = To break out of a loop. For example
for i in range(9):
if i > 3:
break
print(i)
class = To define a class. For example
class Person:
name = "Atul"
age = 22
Continue = This keyword is used to end the current iteration in a
for loop (or a while loop) and continues to the next iteration.
For
Example
for i in range(9):
if i == 3:
continue
print(i)
def = def is used to define a function. For example
def myfunction():
print("Hello world!")
myfunction
del = To delete a class. For example
class myclass:
name = "Atul"
del myclass
print(myclass)
output
NameError: name 'myclass' is
not defined
if = This keyword is used to create a conditional statement (if
statement) and allows you to execute a block of code only if a condition is
True.
x = 5
if x > 3:
print("Yes")
elif = This keyword is used in conditional statement and is
short for else if. For example
for i in range(-5, 5):
if i > 0:
print("Yes")
elif i == 0:
print("WHATEVER")
else:
print("No")
else = This is used in also conditional statement. For
example
x = 2
if x > 3:
print("Yes")
else:
print("No")
except = Used with expectations, what to do when an
exception occurs. For example
try:
x > 3
except:
print("Something went wrong")
print("Even if it is raised an error, the program keeps running")
NOTE = (x>3) will raise an error because x is not defined.
output
- Something went wrong...even if it raised an error, the program keeps
running.
global = Declare a global variable inside a function and use it
outside the function. For example
def myfunction():
global x
x = "hello Atul"
myfunction()
print(x)
import = import the datetime module and display the current date
and time. For example
import datetime
x = datetime.datetime.now()
print(x)
in = The in keywork is used to check if a value is present
in a sequence (list, range and string etc)
The "in" keyword
is also used to iterate thorugh a sequence in a for loop.
fruits = ["apple", "banana", "cheery"]
if "banana" in fruits:
print("Yes")
lambda keyword = The lambda keyword is used to create small
anonymous functions.
lambda function can take any number of
argument, but can only have one expression.
x = lambda a : a + 10
print(x)
Python Identifiers
Python identifiers is the name we give to identify a variable, function class
module or other object. This means whenever we want to give an entity a name,
thats called identifier.
so,
myvariable
variable_1
variable_for_print
-
An identification start with the digit, so while variable1 is valid,
1variable is not valid.
-
We cant use special symbol !, #, @, %, $, etc in our identifiers.
For Example
x = int(input("Enter first number"))
y = int(input("Enter second number"))
sum = x + y
print("The sum of x and y is " , sum)
Q) wap to validate the credentials using python with userid and password
def login():
userid = input("Enter userid")
pwd = input("Enter password")
if(userid == "Atul" and pwd == "akku"):
print("You are a valid user")
else:
print("You are not a valid user")
login()
Q) wap to display a largest number in python using(if, elif, else)
def largest():
x = int(input("Enter the value of x \n"))
y= int(input("Enter the value of y \n"))
z = int(input("Enter the value of z \n"))
if(x >= y and y >= z):
print("x is greater than y")
elif(y > x and y > z):
print("y is greater than z")
else:
print("z is greater than of all among of them")
largest()
List and its function
List is a data type function which store any types of data such as
integer, number, string etc.
There is a so many functions in this list -
- append()
- insert()
- clear()
- count()
- copy()
- copy()
- remove()
- index()
- reverse()
- extend()
append() = It is a function is used to
insert an element and ethe end of the list.
i = [5, 10, 15, 8, 21]
i.append(30)
print(i)
output
[5, 10, 15, 8, 21, 30]
Insert = It is used to insert an element in a specific position
in the insert(). Its contains two argument so first contains index number and
second the elements.
i = [5, 10, 15, 8, 21]
i.insert(2, 6)
print(i)
output
[5, 10, 6, 15, 8, 21]
clear() = clear function is used to remove all the elements from
the list.
i = [5, 10, 15, 8, 21]
i.clear()
print(i)
output
[]
count() = It is used to count the number of times an element
appear in the list. In this function we have to pass the elements name.
i = [5, 10, 15, 8, 10 21]
i.count(10)
print(i)
output
2
copy = copy is used to copy one list into another list.
i = [5, 10, 15, 8, 10 21]
j.copy()
print(j)
output
[5, 10, 15, 8, 10 21]
pop() = pop() function is used to remove an elements from
specific position by passing its index number.
i = [5, 10, 15, 8, 21]
i.pop(2)
print(i)
output
[5, 10, 8,21]
remove() = remove function is used to remove an elements by
passing the elements name in function.
i = [5, 10, 15, 8, 21]
i.remove(10)
print(i)
output
[5, 15, 8, 21]
index()
= index() function is used to display the index number or position on the
elements in the list. In this function we have to pass the elements name.
i = [5, 10, 15, 8, 21]
i.index(15)
print(i)
output
2
reverse() = reverse() function is used to reverse all of the
elements in a list.
i = [5, 10, 15, 8, 21]
i.reverse()
print(i)
output
[21, 8, 15, 10, 5]
extend() = extend() is used to insert all the elements in the
last position in the list.
i = [5, 10, 15, 8, 21]
name = ["atul", "hackingtruth"]
i.extend(name)
print(i)
sort() = sort function is used to sort the elements in ascending
order or descending order. By default, sort function store the
elements
in ascending order. If we want to display the elements in descending order
then we have to use (reverse=true)
i = [5, 10, 15, 8, 21]
i.sort()
print(i)
output
[5, 8, 10, 15, 21]
In Descending order
i = [5, 10, 15, 8, 21]
i.sort(reverse=true)
print(i)
output
[21, 15, 10, 8, 5]
Dictionary and its function
- Dictionary are used to store data values in key: value pairs.
- Dictionary are written with curly brackets and have keys and values.
- Dictionary items are ordered.
-
Dictionary are changeable meaning that we can change add or remove items
after the dictionary has been created.
- Duplicates values are not allowed.
- Dictionary cannot have two items with the same keys.
- clear()
- copy()
- get(keyname)
- fromkeys()
- keys()
- values()
- items()
- pop()
- popitems()
- update()
clear() = clear methods are used to remove all the elements
from the dictionary list.
cybersecurity = {
"brand" : "Hacking Truth",
"domain" : "hackingtruth.org",
"service" : "penetration testing"
}
cybersecurity.clear()
output
{}
copy() = copy function is used to copy one dictionary into
another dictionary object.
a = {"science" : 67, "maths" : 89}
b = a.copy()
print(a)
print(b)
output
{"science" : 67, "maths" : 89}
{"science" : 67,
"maths" : 89}
get() = The get method returns the value of the item with the
based on key.
car = {
"brand" : "BMW",
"model" : "Mustand",
"year" : "1964"
}
x = car.get("model")
print(x)
output
mustang
fromkey() = It is used to create a dictionary based on the key
variable and values variable.
key = [1, 2, 3]
value = {"java", "c++", "android"}
dict = fromkeys(key, value)
print(dict)
output
1 : "java", 2 : "c++", 3 : "android"
keys() = It is used to returns all the keys from the
dictionary.
dict = {a : "atul", b : "kumar"}
print(dict.keys())
output
dict_keys(['a', 'b'])
values() = values is used to return all the value from the
dictionary.
dict = {1: "java", 2: "c++", 3: "android"}
value = dict.values()
print(value)
output
(["java", "c++", "android"])
item() = item() is used to return all the keys and value
dict = {1: "java", 2: "android"}
item = dict.items()
print(item)
pop() = pop() is used to remove an element based on the key
path.
hisdict = {
"brand" : "ford",
"model" : "mustand",
"year" : "1964"
}
hisdict.popitem()
print(hisdict)
output
{"brand" : "ford", "model" : "mustand"}
Conditional construct
In conditional construct python is a block of executed condition
become true if condition is becoming not true if check all the elif blocks
If
any of one elif block become true it will print the statement of respective
elif block.
If none of the elif block becming true it executes the
else block to define the condition construct. We have to write if inside the
paramter and terminate will colon (:) symbol.
if(avg >= 75):
The body of the construct starts with indentation or
block space is space of curly braces.
sub1 = int("Enter the marks of student1")
sub2 = int("Enter the marks of student2")
sub3 = int("Enter the marks of student3")
avg = (sub1 + sub2 + sub3)/3
if(avg >= 75):
print("Grade A")
elif(avg >= 60 and avg < 75):
print("Grade B")
elif(avg >= 50 and avg < 60):
print("Grade C")
else:
print("Grade D")
For loop = for i in marks:
i = variable (iterate,
traverse)
marks = sequence(list, tuple)
In python for loop is used to iterate or traverse in the element of
sequence. The sequence can be list tuple, list, dictionary or any string data
type. We can stop the execution of for loop by using the break statement.
We
can also give else block in for statement and the else block will block when
all the condition becomes false even break statement also.
For example1
num = [5, 10, 15 ,20]
for i in num:
print(i)
For example2
num = [5, 10, 15, 20]
sum = 0
for i in num:
sum = sum + i
print("sum is " , sum)
marks = {"Atul" : 85, "hackingtruth" : 99}
name = input("Enter a name")
for student in marks:
if(student == name):
print(marks[student])
break
else:
print("No such name exit")
Practical Question
1Q) wap to add, mul, sub, divide using function ?
#!/usr/bin/python
a = int(input("Enter first value : "))
b = int(input("Enter second value : "))
def add():
c = a + b
# a = 5 + 5
print("The sum of a and b is : " , c)
def sub():
c = a - b
# b = 5 - 5
print("The subtraction of a and b is : " , c)
def mul():
c = a * b
# c = 5 * 5
print("The multiplication of a and b is : " , c)
def div():
c = a / b
# d = 5 / 5
print("The division of a and b is : " , c)
add()
sub()
mul()
div()
2Q) wap to validate a user using dictionary?
#!/usr/bin/python
Dict = {"atul" : "atul143", "hackerboy" : "hackerboy143" }
a = input("Enter the username : ")
b = input("Enter the password : ")
if a and b not in Dict:
print("You are a valid user")
else:
print("You are not a valid user")

3Q) wap to using Tk() function interface to add the number?
from tkinter import *
win = Tk()
win.geometry("400x400")
Label(win, text="Your First Number:").grid(row=0, column=0)
Label(win, text="Your Second Number:").grid(row=1, column=0)
# define the label, step 1
label3 = Label(win)
# set grid, step 2
label3.grid(row=3, column=1)
first_no = IntVar()
second_no = IntVar()
# same goes for here
e1 = Entry(win, textvariable=first_no).grid(row=0, column=1)
e2 = Entry(win, textvariable=second_no).grid(row=1, column=1)
def add():
sum = first_no.get() + second_no.get()
label3.config(text="your final number is:" + str(sum))
mybutton = Button(win, text=("Calculate!"), command=add).grid(row=2, column=1)
win.mainloop()
5Q) wap in python using append, remove, reverse and extend list item?
#!/usr/bin/python
listitem = [5, 10, 15, 8, 21]
print("Before performing the operation " , listitem)
#append
listitem.append(30)
print("After appending some values : " , listitem)
#remove
listitem.remove(15)
print("Now, Removing 15 no element from list : " , listitem)
#
#reverse
listitem.reverse()
print("After reversing values : " , listitem)
#extend
name = ["atul", "hackingtruth"]
listitem.extend(name)
print("after using extending func : " , listitem)

6Q) wap to insert product ID, product name and product price in list date
types and display it?
#!/usr/bin/python
pid = int(input("Enter the product id (1, 2, 3...) : "))
pname = input("Enter the product name : ")
pprice = input("Enter the product price : ")
list1 = []
list1.append(pid)
list1.append(pname)
list1.append(pprice)
print(list1)
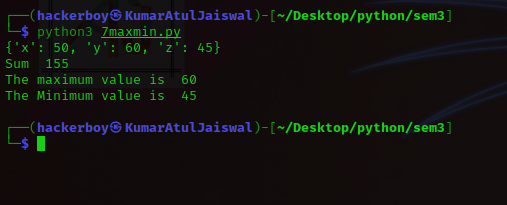
7Q) wap to create a dictionary and add all of the value and also display
maximum and minimum value?
#!/usr/bin/python
Dict = {"x" : 50, "y" : 60, "z" : 45}
print(Dict)
total = 0
for i in Dict.values():
total = total + i
print("Sum " , total)
print("The maximum value is " , max(Dict.values()))
print("The Minimum value is " , min(Dict.values()))
8Q) create a dictionary and add some item in dictionary and display it?
#!/usr/bin/python3
a = input("Enter the key attribute name : ")
b = input("Enter the value of key attribute : ")
Dict = {}
Dict.update({a : b})
print(Dict)

Disclaimer
All tutorials are for informational and educational purposes only and have
been made using our own routers, servers, websites and other vulnerable free
resources. we do not contain any illegal activity. We believe that ethical
hacking, information security and cyber security should be familiar subjects
to anyone using digital information and computers. Hacking Truth is against
misuse of the information and we strongly suggest against it. Please regard
the word hacking as ethical hacking or penetration testing every time this
word is used. We do not promote, encourage, support or excite any illegal
activity or hacking.


























