Tshark
Bored with trying to extract packets by hand? Need to get info from a pcap
file that doesn't extract easily from Wireshark? Are GUIs for losers but now
you realized you can't open Wireshark? Well my friend, TShark is the solution
to all your problems.
Installation
Before beginning, we need to make sure we have
tshark installed on our host - If you are using the AttackBox you can skip this, as
it already has tshark installed.
Generally, tshark is installed with
Wireshark. But let's verify it's installed anyway. Run the command below to determine
if it's installed or not.
apt list tshark
In my output above, we can
see that it is installed. If it's not installed, sudo apt install tshark will
do the trick.
The tshark program is also available in a Windows
installation as tshark.exe in the Wireshark install
directory.
Try running tshark -h to get the help output to make sure we can access the program properly.
Download Capture File :- Click Here
Download Capture File :- Click Here
This task uses the
dns.cap capture file on the Wireshark SampleCaptures wiki page.
To read a
file with TShark, we will use the -r switch. This will display a summary line
of each packet similar to tcpdump output and is useful to identify high-level
information about the capture.
tshark -r dns.cap
When paired with wc -l, we can quickly identify how
many packets are in a capture.
tshark -r dns.cap | wc -l
We can utilize Wireshark display filters (which
are DIFFERENT than bpf syntax) to narrow down what packets are displayed. If
we're interested in DNS A records only, we can use the dns.qry.type == 1
display filter to narrow down our packets. Display filters are added using the
-Y switch. Our command below will show all of the A records in our capture,
including responses.
tshark -r dns.cap -Y "dns.qry.type == 1"
The power of TShark comes with
combining traditional Wireshark filters with extraction. We can extract specific field values directly from
the pcap, allowing us to have only the interesting fields returned. One way to
extract data is using the
-T fields and -e [fieldname] switches. To extract the A records in the pcap, we would use -T fields -e
dns.qry.name at the end of our previous tshark command. This makes our command
the one below:
tshark -r dns.cap -Y "dns.qry.type == 1" -T fields -e dns.qry.name
NOTE: An easy way to identify field names in Wireshark is to navigate to the Packet Details in the capture, highlight the interesting field, then view the bottom left corner.
1) How many packets are in the dns.cap file?
Command :-
tshark -r cap | wc -l
Ans:- 38
2) How many A records are in the capture? (Including responses)
Command :- tshark -r cap -Y "dns.qry.type == 1"
Ans:- 6
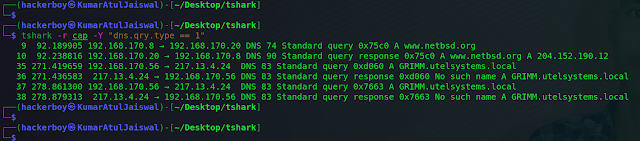
3) Which A record was present the most?
Command :- tshark -r cap -Y "dns.qry.type == 1" -T fields -e
dns.qry.name
Ans:- GRIMM.utelsystems.local
File :- Pcap ( above the link )
The following seven pillars constitute the foundation of this life-changing course:can you find it?
Use the attached file to analyze in Wireshark and TShark to find
the exfiltrated data. As you identify suspicious items in Wireshark, pivot to
TShark to extract relevant information.
Remember, we can filter out irrelevant packets with the -Y switch
using display filters.
1) How many packets are in this capture?
Command :- tshark -r pcap | wc -l
Ans :- 125
2) How many DNS queries are in this pcap? (Not responses!)
Command :- tshark -r pcap -Y "dns.flags.response ==
0" | wc -l
Ans :- 56
3) What is the DNS transaction ID of the suspicious queries (in hex)?
Command :- tshark -r pcap -Y "dns.qry.type == 1"
Ans :- 0xbeef
4) What is the string extracted from the DNS queries?
Command :- tshark -r pcap -Y "dns.qry.type == 1" | grep -v
'unreachable' | cut -d 'A' -f 2 | cut -d '.' -f 1
MMZZWWGGCCZZ3333OORRUUDDCC442277NNFFZZVV6655BQQBOOV
VTTWWQQXX33XXNNFF22GGQQMMDDVVGG55PPXXII4433IIGGRRZZ
remove the duplicates (e.g. MM -> M, 3333 -> 33) leaves us with:
Ans :- MZWGCZ33ORUDC427NFZV65BQOVTWQX3XNF2GQMDVG5PXI43IGRZGWIL5
5) What is the flag?
Command
echo
"MZWGCZ33ORUDC427NFZV65BQOVTWQX3XNF2GQMDVG5PXI43IGRZGWIL5" | base32 -d
Ans :- flag{th1s_is_t0ugh_with0u7_tsh4rk!}
Optional for this post (wireshark) - Put http.request.method == "POST" in the display filter of wireshark to only show POST requests. Click on the packet, then expand the Hypertext Transfer Protocol field. The POST data will be right there on top.
Disclaimer
This was written for educational purpose and pentest only.
The author
will not be responsible for any damage ..!
The author of this tool is not
responsible for any misuse of the information.
You will not misuse the
information to gain unauthorized access.
This information shall only be
used to expand knowledge and not for causing malicious or damaging
attacks. Performing any hacks without written permission is illegal ..!
All
video’s and tutorials are for informational and educational purposes only. We
believe that ethical hacking, information security and cyber security should
be familiar subjects to anyone using digital information and computers. We
believe that it is impossible to defend yourself from hackers without knowing
how hacking is done. The tutorials and videos provided on www.hackingtruth.in
is only for those who are interested to learn about Ethical Hacking, Security,
Penetration Testing and malware analysis. Hacking tutorials is against misuse
of the information and we strongly suggest against it. Please regard the word
hacking as ethical hacking or penetration testing every time this word is
used.
All tutorials and videos have been made using our own
routers, servers, websites and other resources, they do not contain any
illegal activity. We do not promote, encourage, support or excite any illegal
activity or hacking without written permission in general. We want to raise
security awareness and inform our readers on how to prevent themselves from
being a victim of hackers. If you plan to use the information for illegal
purposes, please leave this website now. We cannot be held responsible for any
misuse of the given information.
- Hacking Truth by
Kumar Atul Jaiswal
I hope you liked this post, then you
should not forget to share this post at all.
Thank you so much :-)














