The platform develops virtual classrooms that not only allow users to deploy training environments with the click of a button, but also reinforce learning by adding a question-answer approach. Its a comfortable experience to learn using pre-designed courses which include virtual machines (VM) hosted in the cloud.
tryhackme rp nmap
While using a question-answer model does make learning easier, TryHackMe allows users to create their own virtual classrooms to teach particular topics enabling them to become teachers. This not only provides other users with rich and varied content, but also helps creators reinforce their understanding of fundamental concepts.
Script Categories :- Click Here
TryHackMe :- Click Here
TryHackMe has recently had their 500th user sign up to access varied content from fundamentals of web security to basic reverse engineering. Their self contained virtual classrooms make it easy for users to focus on a particular area by aggregating the necessary information. They want users to focus on the learning instead of spending time scouring the internet for resources! They are a relatively new company, so they are still in the process of creating custom VMs for learning purposes, but more content is being released weekly and their newsletter gives users an insight to whats being released on a weekly basis ahead of time.
Question:
1) First, how do you access the help menu?
-h
2) Often referred to as a stealth scan, what is the first switch listed for a ‘Syn Scan’?
--sS
3) Not quite as useful but how about a ‘UDP Scan’?
--sU
4) What about operating system detection?
--O
5) How about service version detection?
--sV
6) Most people like to see some output to know that their scan is actually doing things, what is the verbosity flag?
--v
7) What about ‘very verbose’? (A personal favorite)
--vv
8) Sometimes saving output in a common document format can be really handy for reporting, how do we save output in xml format? -oX
--oX
9) Aggressive scans can be nice when other scans just aren’t getting the output that you want and you really don’t care how ‘loud’ you are, what is the switch for enabling this?
-A
10) How do I set the timing to the max level, sometimes called ‘Insane’?
-T5
11) What about if I want to scan a specific port?
-P
12 )How about if I want to scan every port?
-p-
13) What if I want to enable using a script from the nmap scripting engine? For this, just include the first part of the switch without the specification of what script to run.
--script
14) What if I want to run all scripts out of the vulnerability category?
--script vuln
15) What switch should I include if I don’t want to ping the host?
-Pn
Nmap Scanning
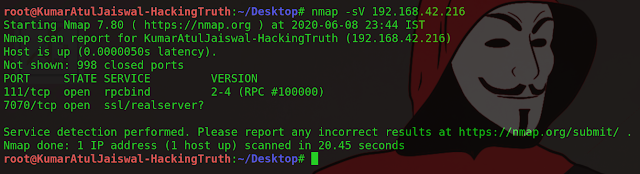
1) Let’s go ahead and start with the basics and perform a syn scan on the box provided. What will this command be without the host IP address?
nmap -sS
2) After scanning this, how many ports do we find open under 1000?
ANS : 2
3) What communication protocol is given for these ports following the port number?
ANS : tcp
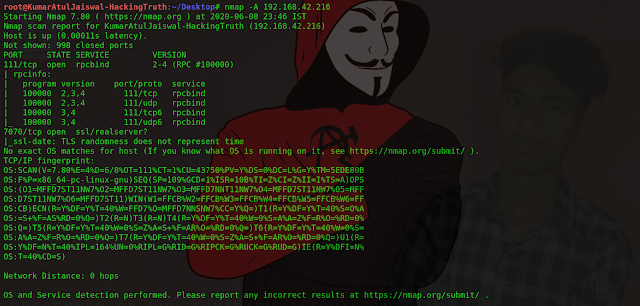
4) Perform a service version detection scan, what is the version of the software running on port 22?
nmap -sV <ip>
ANS : 6.6.1p1
5) Perform an aggressive scan, what flag isn’t set under the results for port 80?
nmap -A <ip>
ANS: httponly
6) Perform a script scan of vulnerabilities associated with this box, what denial of service (DOS) attack is this box susceptible to? Answer with the name for the vulnerability that is given as the section title in the scan output. A vuln scan can take a while to complete. In case you get stuck, the answer for this question has been provided in the hint, however, it’s good to still run this scan and get used to using it as it can be invaluable.
nmap --script vuln <ip>
ANS: http-slowloris-check
Disclaimer
This was written for educational purpose and pentest only.The author will not be responsible for any damage ..!
The author of this tool is not responsible for any misuse of the information.
You will not misuse the information to gain unauthorized access.
This information shall only be used to expand knowledge and not for causing malicious or damaging attacks. Performing any hacks without written permission is illegal ..!
All video’s and tutorials are for informational and educational purposes only. We believe that ethical hacking, information security and cyber security should be familiar subjects to anyone using digital information and computers. We believe that it is impossible to defend yourself from hackers without knowing how hacking is done. The tutorials and videos provided on www.hackingtruth.in is only for those who are interested to learn about Ethical Hacking, Security, Penetration Testing and malware analysis. Hacking tutorials is against misuse of the information and we strongly suggest against it. Please regard the word hacking as ethical hacking or penetration testing every time this word is used.
All tutorials and videos have been made using our own routers, servers, websites and other resources, they do not contain any illegal activity. We do not promote, encourage, support or excite any illegal activity or hacking without written permission in general. We want to raise security awareness and inform our readers on how to prevent themselves from being a victim of hackers. If you plan to use the information for illegal purposes, please leave this website now. We cannot be held responsible for any misuse of the given information.
Video Tutorial :-
I hope you liked this post, then you should not forget to share this post at all.
Thank you so much :-)