Sakura Room
Use a variety of OSINT techniques to solve this room created by the OSINT
Dojo.
OSINT Dojo’s Sakura Room walkthrough
Welcome to the OSINT Dojo’s Sakura Room!
Task 2 TIP-OFF
Background
The OSINT Dojo recently found themselves the
victim of a cyber attack. It seems that there is no major damage, and there
does not appear to be any other significant indicators of compromise on any of
our systems. However during forensic analysis our admins found an image left
behind by the cybercriminals. Perhaps it contains some clues that could allow
us to determine who the attackers were?
We've copied the
image left by the attacker, you can view it in your browser here.
Instructions
Images can contain a treasure trove of information, both on
the surface as well as embedded within the file itself. You might find
information such as when a photo was created, what software was used, author
and copyright information, as well as other metadata significant to an
investigation. In order to answer the following question, you will need to
thoroughly analyze the image found by the OSINT Dojo administrators in order
to obtain basic information on the attacker.
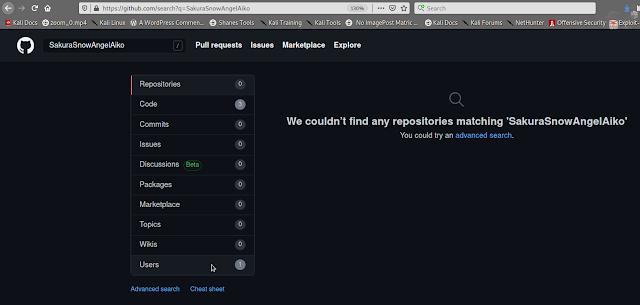
open image link and press ctrl+u

1) What username does the attacker go by?
Ans :-
SakuraSnowAngelAiko
Task 3 RECONNAISSANCE
Background
It appears that our attacker made a fatal
mistake in their operational security. They seem to have reused their username
across other social media platforms as well. This should make it far easier
for us to gather additional information on them by locating their other social
media accounts.
Instructions
Most digital platforms
have some sort of username field. Many people become attached to their
usernames, and may therefore use it across a number of platforms, making it
easy to find other accounts owned by the same person when the username is
unique enough. This can be especially helpful on platforms such as on job
hunting sites where a user is more likely to provide real information about
themselves, such as their full name or location information.
A
quick search on a reputable search engine can help find matching usernames on
other platforms, and there are also a large number of specialty tools that
exist for that very same purpose. Keep in mind, that sometimes a platform will
not show up in either the search engine results or in the specialized username
searches due to false negatives. In some cases you need to manually check the
site yourself to be 100% positive if the account exists or not. In order to
answer the following questions, use the attacker's username found in Task 2 to
expand the OSINT investigation onto other platforms in order to gather
additional identifying information on the attacker. Be wary of any false
positives!
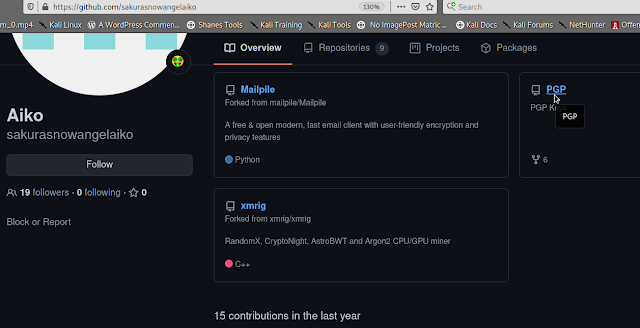
–>Goto github and search ‘SakuraSnowAngelAiko’ username
–>Under that user you will find PGP repo
–>you can copy this code and decode using base64
echo "public key" | base64 -d
Public key Link here :-
Click Here
1) What is the full email address used by the attacker?
Ans
:- SakuraSnowAngel83@protonmail.com
2) What is the attacker's full real name?
Ans :- Aiko
Abe
Task 4 UNVEIL
Background
It seems the cybercriminal is aware that we
are on to them. As we were investigating into their Github account we observed
indicators that the account owner had already begun editing and deleting
information in order to throw us off their trail. It is likely that they were
removing this information because it contained some sort of data that would
add to our investigation. Perhaps there is a way to retrieve the original
information that they provided?
Instructions
On some platforms, the edited or removed content may be
unrecoverable unless the page was cached or archived on another platform.
However, other platforms may possess built-in functionality to view the
history of edits, deletions, or insertions. When available this audit history
allows investigators to locate information that was once included, possibly by
mistake or oversight, and then removed by the user. Such content is often
quite valuable in the course of an investigation. In order to answer the below
questions, you will need to perform a deeper dive into the attacker's Github
account for any additional information that may have been altered or removed.
You will then utilize this information to trace some of the attacker's
cryptocurrency transactions.

1) What cryptocurrency does the attacker own a cryptocurrency wallet
for?
Ans :- Ethereum
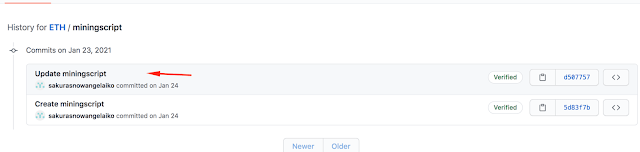
--> Scroll down to see repos in which we can see there is a ETH repo
–> Click on this repo
–> Click on miningscript
–> Click
on history
2) What is the attacker's cryptocurrency wallet address?
Ans
:- 0xa102397dbeeBeFD8cD2F73A89122fCdB53abB6ef
3) What mining pool did the attacker receive payments from on January 23,
2021 UTC?
Ans :- Ethermine
4) What other cryptocurrency did the attacker exchange with using
their cryptocurrency wallet?
Ans :- Tether
Task 5 Taunt
Background
Just as we thought, the cybercriminal is
fully aware that we are gathering information about them after their attack.
They were even so brazen as to message the OSINT Dojo on Twitter and taunt us
for our efforts. The Twitter account which they used appears to use a
different username than what we were previously tracking, maybe there is some
additional information we can locate to get an idea of where they are heading
to next?
We've taken a screenshot of the message sent to us by the
attacker, you can view it in your browser here.
Instructions
Although many users share their username across different
platforms, it isn't uncommon for users to also have alternative accounts that
they keep entirely separate, such as for investigations, trolling, or just as
a way to separate their personal and public lives. These alternative accounts
might contain information not seen in their other accounts, and should also be
investigated thoroughly. In order to answer the following questions, you will
need to view the screenshot of the message sent by the attacker to the OSINT
Dojo on Twitter and use it to locate additional information on the attacker's
Twitter account. You will then need to follow the leads from the Twitter
account to the Dark Web and other platforms in order to discover additional
information.
1) What is the attacker's current Twitter handle?
Ans :- SakuraLoverAiko
HINT :-
Not too concerned about someone else finding them on the Dark Web.
— Aiko (@SakuraLoverAiko) January 24, 2021
Anyone who wants them will have to do a real DEEP search to find where I PASTEd them.
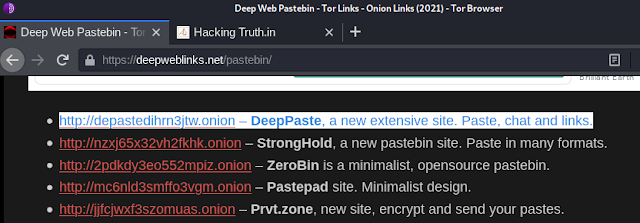
--> Open Tor and search deep paste dark web and go to this - Deep web
pastebin - Tor Links - onion Links (2021)
--> Click on
https://depastedihrn3jtw.onion -
DeepPaste, a new extensive site..
2) What is the URL for the location where the attacker saved their
WiFi SSIDs and passwords?
Ans :-
http://depastedihrn3jtw.onion/show.php?md5=0a5c6e136a98a60b8a21643ce8c15a74
HINT :- wigle.net is a website where we can find wireless network data by
using location, name etc. From the above saved screenshot we got exact name
of wifi. you can goto wigle and register and login, after that you can do
advanced search with the name of wifi.
3) What is the BSSID for the attacker's Home WiFi?
Ans :-
84:af:ec:34:fc:f8
Task 6 HOMEBOUND
Background
Based on their tweets, it appears our
cybercriminal is indeed heading home as they claimed. Their Twitter account
seems to have plenty of photos which should allow us to piece together their
route back home. If we follow the trail of breadcrumbs they left behind, we
should be able to track their movements from one location to the next back all
the way to their final destination. Once we can identify their final stops, we
can identify which law enforcement organization we should forward our findings
to.
Instructions
In OSINT, there is
oftentimes no "smoking gun" that points to a clear and definitive answer.
Instead, an OSINT analyst must learn to synthesize multiple pieces of
intelligence in order to make a conclusion of what is likely, unlikely, or
possible. By leveraging all available data, an analyst can make more informed
decisions and perhaps even minimize the size of data gaps. In order to answer
the following questions, use the information collected from the attacker's
Twitter account, as well as information obtained from previous parts of the
investigation to track the attacker back to the place they call home.
1) What airport is closest to the location the attacker shared a photo from
prior to getting on their flight?
Ans :- DCA
2) What airport did the attacker have their last layover in?
Ans :- HND
3) What lake can be seen in the map shared by the attacker as they were on
their final flight home?
Ans :- Lake Inawashiro
4) What city does the attacker likely consider "home"?
Ans :- Hirosaki
Disclaimer
This was written for educational purpose and pentest only.
The author will not be responsible for any damage ..!
The author of this tool is not responsible for any misuse of the information.
You will not misuse the information to gain unauthorized access.
This information shall only be used to expand knowledge and not for causing malicious or damaging attacks. Performing any hacks without written permission is illegal ..!
All video’s and tutorials are for informational and educational purposes only. We believe that ethical hacking, information security and cyber security should be familiar subjects to anyone using digital information and computers. We believe that it is impossible to defend yourself from hackers without knowing how hacking is done. The tutorials and videos provided on www.hackingtruth.in is only for those who are interested to learn about Ethical Hacking, Security, Penetration Testing and malware analysis. Hacking tutorials is against misuse of the information and we strongly suggest against it. Please regard the word hacking as ethical hacking or penetration testing every time this word is used.
All tutorials and videos have been made using our own routers, servers, websites and other resources, they do not contain any illegal activity. We do not promote, encourage, support or excite any illegal activity or hacking without written permission in general. We want to raise security awareness and inform our readers on how to prevent themselves from being a victim of hackers. If you plan to use the information for illegal purposes, please leave this website now. We cannot be held responsible for any misuse of the given information.
- Hacking Truth by Kumar Atul Jaiswal
I hope you liked this post, then you should not forget to share this post at all.
Thank you so much :-)