In this room, you will be learning social media analysis and forensics. You will learn about google dorking, website archiving, social media enumeration/analysis, and the basic usage of OSINT techniques in the context of social media investigation. You don't need any previous knowledge of OSINT to do well in this room, but it definitely helps. I have included some resources in the "Resources" task at the bottom of the room that I encourage you to check out after completing this room!
Prerequisites:
Critical Thinking.
A love of going deep into rabbit
-holes.
Basic understanding of Google.
Python 3.7+
Task 2 Story
Background Information:
You are Aleks Juulut, a private eye based out of Greenland. You don't usually work digitally, but have recently discovered OSINT techniques to make that aspect of your job much easier. You were recently hired by a mysterious person under the moniker "H" to investigate a suspected cheater, named Thomas Straussman. TryHackMe KaffeeSec - SoMeSINT
After a brief phone-call with his wife, Francesca Hodgerint, you've learned that he's been acting suspicious lately, but she isn't sure exactly what he could be doing wrong. She wants you to investigate him and report back anything you find. Unfortunately, you're out of the country on a family emergency and cannot get back to Greenland to meet the deadline of the investigation, so you're going to have to do all of it digitally. Good luck!
Answer the questions below
1) Who hired you?
Ans :- ks{H}
2) Who are you investigating? (ks{firstname lastname})
Ans :- ks{thomas straussman}
Task 3 Let's get started!!
Prerequisites:
Patience, curiosity, and a passion for digging into rabbit holes.
Firefox, Chrome, or another chromium-based browser (I recommend Brave).
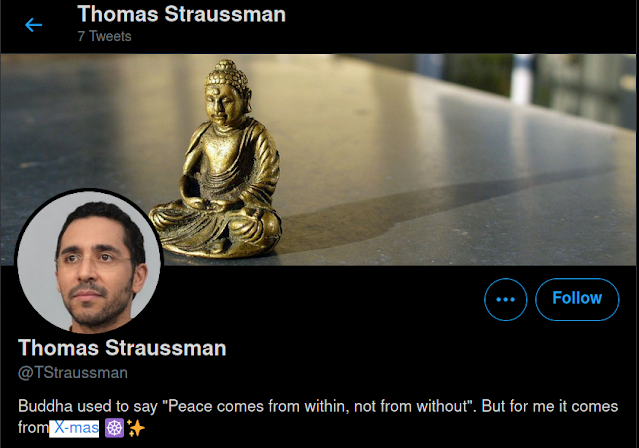
How exciting! Through talking to people who know Thomas, you've found out that he has a very guessable online handle: tstraussman. With this handle, we can find his social media accounts.
The overall process for finding information from social media accounts starts with finding the social media accounts themselves. Finding social media accounts from names or emails can be automated through a process called enumeration. This is usually done with CLI tools or scripts, but you can get similar effects with google dorking. Here is a guide on google dorking, it's great reading material before you attempt this task and also includes a cheat-sheet that comes in handy.
Before starting, I will preface this by saying the only places these accounts are found on are Twitter and Reddit. Please do not try to investigate further out-of-scope, as you will both meet a dead end and be snooping on accounts not involved with this CTF at all. I am not responsible for any actions/interactions made with an account outside of the sockpuppets created for this CTF. As a general rule, we're collecting PASSIVE information - there's no interacting directly with these accounts.
Answer the questions below
1) What is Thomas' favorite holiday?
Ans :- Christmas
2) What is Thomas' birth date?
Ans :- 12-20-1990
3) What is Thomas' fiancee's Twitter handle?
Ans :- @fhodgelink
4) What is Thomas' background picture of?
Ans :- Buddha
Task 4 Spider... what?
Requirements:
Spiderfoot
Python 3
First things first, make sure that you've downloaded the latest version of Python3. Then follow this guide to install the latest version of Spiderfoot (currently v3.3).
Once it's installed correctly, run it by typing python3 sf.py -l 127.0.0.1:5001
You can access the web interface by navigating to localhost:5001 in your browser.
Click on "New Scan". In the "Scan Target" field, type in "Thomas Straussman" or "tstraussman"; then, under By Use Case, ensure that you checked the All option. Finally, press run.
Looking at the results, you can figure out which are false positives by filtering out anything that isn't related to Reddit or Twitter.
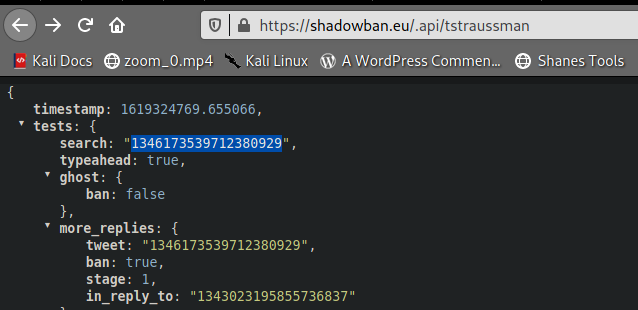
If you find a Twitter account that leads to shadowban.eu, click on the link.
If you can't find anything related to Twitter, go to Settings --> Account Finder and set the highlighted option to False.
1) What was the source module used to find these accounts?
Ans :- sfp_accounts
2) Check the shadowban API. What is the value of "search"?
Ans :- ks{1346173539712380929}
Task 5 Connections, connections..
Now that you have Thomas' Reddit and Twitter accounts, you can do some cool stuff!
At this point, consider downloading a reverse search extension for your browser, my favorite is RevEye, which lets you choose from a handful of great reverse search engines, or use all of them simultaneously. Chrome / Firefox
There are a few key types of information that we want to find from socials:
Images of places that contain clear identifiers like buildings, signs, monuments, or landmarks (For IMINT/GEOMINT purposes).
Clear images of the subject's face (For reverse image searches and possibly finding more accounts/sources of info).
Clear images of the subject in a group of people (Family photos, friend groups, other information that can give context to their relationship with the group).
Personal information in their bio, or other personal data from their profile itself (Where they grew up, currently live, went to school, etc..).
Relevant posts that may contain information on their whereabouts or personal habits (Do they smoke? Drink? Go to bars often? Love to vacation to specific places? All this information can help in an investigation.)
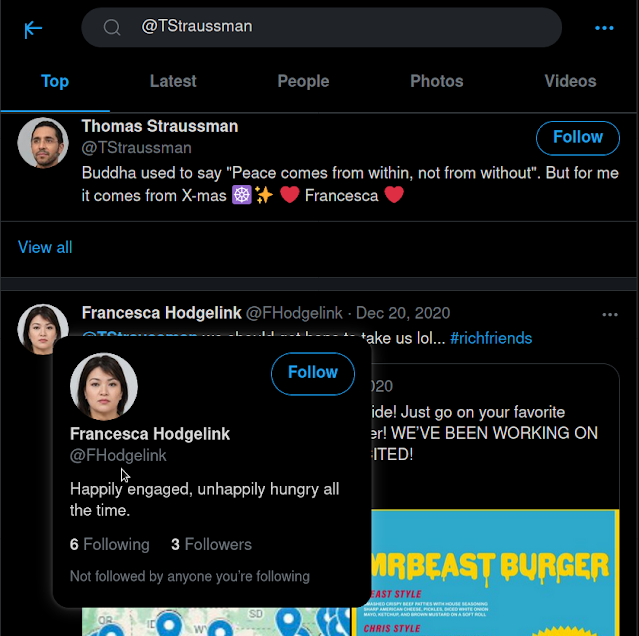
Since you have gotten most useful information from Thomas' Twitter, it's time to "pivot" to his fiancee's account.
What personal information can you find?
NOTE: If you get stuck on the first flag, consider two things:
- You can reverse image search landscapes / locations and most likely get a result.
- You can look at the source of the website (ctrl + shift + c, then click on the image) and try to find some metadata from the image.
Answer the questions below
1) Where did Thomas and his fiancee vacation to?
Ans :- Koblenz, Germany
So,it will be in the format — — — -, Germany.
Doing a reverse search of this image, indicates its Koblenz in Germany.

2) When is Francesca's Mother's birthday? (without the year)
Ans :- Decemeber 25th
3) What is the name of their cat?
Ans :- Gotank
4) What show does Francesca like to watch?
Ans :- 90 Day Fiancee
Task 6 Turn back the clock!!
Now that we've gathered intel from Thomas and Francesca's Twitters, lets move to another platform - Reddit.
For the sake of this investigation, we're going to be using Reddit in two different ways:
Use the old version (http://old.reddit.com/) for wayback machine purposes
Use the new version (https://www.reddit.com/) for other purposes (later on)
First, you're going to want to install the WayBackMachine extension for your browser (you don't need it, but it'll make your life much easier).
Get it for Firefox
Get it for Chrome
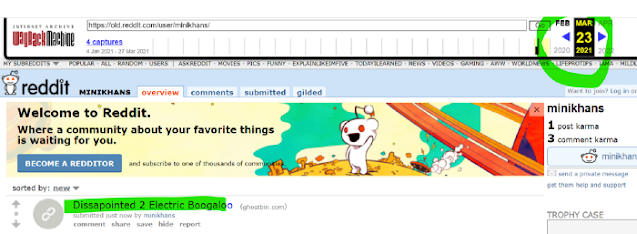
Using Reddit's old site, navigate to Thomas' profile. Right click anywhere on the page and click on Wayback machine --> All Versions. You will see a calendar that shows all of the saved versions of the site, click through and take a look at each saved version (in this case there should be none).
So it hasn't been saved yet... Nothing out of the ordinary, right?
Next, go to Thomas' birthday post. Repeat the steps to find the first version of the site and..... Voila!
We've discovered a coworker, which is another source of intel for us! But the question is... how much intel?
Answer the questions below
1) What is the name of Thomas' coworker?
Ans :- Hans Minik
2) Where does his coworker live?
Ans :- Nuuk, Greenland
Thomas lives in Nuuk, as per his profile
Looking into Hans reddit profile, we can find the following posts
3) What is the paste ID for the link we found? (flag format)
Ans :- ks{ww4ju}
Hans profile is https://web.archive.org/web/20210104143852/https://old.reddit.com/user/minikhans
4) Password for the next link? (flag format)
Ans :- ks{1qaz2wsx}
5) What is the name of Thomas' mistress?
Ans :- Emilia Moller
Paste the password obtained in above step to the url and the name will be shown.
6) What is Thomas' Email address?
Ans :- straussmanthom@mail.com
Disclaimer
All tutorials are for informational and educational purposes only and
have been made using our own routers, servers, websites and other
vulnerable free resources. we do not contain any illegal activity. We
believe that ethical hacking, information security and cyber security
should be familiar subjects to anyone using digital information and
computers. Hacking Truth is against misuse of the information and we
strongly suggest against it. Please regard the word hacking as ethical
hacking or penetration testing every time this word is used. We do not
promote, encourage, support or excite any illegal activity or hacking.
- Hacking Truth by Kumar Atul
Jaiswal